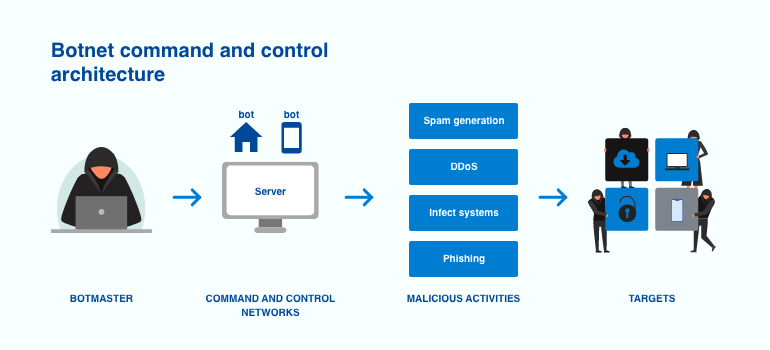
What is a botnet attack and how does it work?
A botnet attack is a type of cyberattack that occurs when a group of internet-connected devices becomes infected with software controlled by a malevolent hacker. Botnet assaults often involve spamming, data theft, stealing sensitive information, or conducting devastating DDoS attacks. The proliferation of gadgets is one of the most significant obstacles in preventing these attacks. As more devices become available, monitoring, detecting, and stopping botnet attacks becomes increasingly complex.
Botnet attacks often begin when attackers acquire unauthorized access to devices through the injection of Trojan malware or the use of basic social engineering techniques. Once hackers get access to these devices, they are controlled by software that allows them to carry out assaults.
What are the most prevalent botnet attacks?
Botnet attacks can vary based on the methods and tools they employ. Let’s take a closer look at some of the common types of botnet attacks.
Phishing attacks
Phishing attacks are a type of attack that uses social engineering strategies to persuade a person to do something that allows the criminal to gain their personal information. For example, hackers may send people emails that look to be from a reputable source in order to fool them into passing over private information such as passwords and bank information.
Distributed Denial-of-Service (DDoS) attacks
One of the more common types of botnet attacks is a DDoS attack – which is carried out by having bots overload a server with web traffic in order to crash it. The downtime in the server’s operation caused by bots can also be exploited by launching additional botnet attacks.
Brute force attacks
Brute force attacks refer to a hacker using a trial-and-error method to guess login information, and encryption keys or find hidden web pages. These attacks are carried out by ‘brute force’ meaning they use excessive attempts to ‘force’ their way into your private accounts.
How can businesses prevent botnet attacks?
Read on to learn more about different preventive measures you can take to protect your organization against botnet attacks.
Ensure all systems are updated
Botnets usually successfully access and compromise networks by exploiting unpatched vulnerabilities in the machines that make up the networks. As a result, it is critical to update your systems on a regular basis and to ensure that new updates are implemented as soon as they become available. Keep in mind that your hardware devices, particularly older devices, should be updated even if they are no longer regularly used.
Maintain good cybersecurity hygiene
It is important to practice good cybersecurity hygiene to protect yourself against botnet attacks. This involves a variety of best practices that you can adopt – such as using hard-to-crack passwords, implementing employee awareness training, and ensuring new devices that enter the network have solid security settings.
Establish control access to machines and systems
Controlling access to machines and systems is another effective way to keep botnet attacks at bay. Not only should you use complex passwords, but you can also deploy multi-factor authentication and controls to provide access only to authorized users. When you control access and separate critical systems from each other, it’s easier to know exactly where the botnet attacks are located and eradicate them.
Continuously monitor network traffic
Preventing botnet attacks requires organizations to effectively detect them ahead of time. Organizations can use advanced analytics to continuously monitor and control traffic flows, user access, and data leaks.
Require cybersecurity training for employees
Employees open emails from unfamiliar senders, mistakenly click on harmful links, and improperly manage sensitive information. This happens more frequently than you might think. The average employee has access to 11 million files, in fact. Your company is quite exposed if your staff members are not properly trained in identifying and responding to threats. To defend themselves and the organization against assaults, botnet or not, employees need cybersecurity training. You can fortify the weakest links in the chain by educating staff about various botnet attacks and the steps to take when danger is identified.
How SecurityScorecard can help
Botnets are difficult to stop once they’ve penetrated and taken root in users’ devices. It’s important to adopt those best practices listed above to prevent botnet attacks or minimize the damage they may cause. It’s also crucial to continuously monitor your systems and networks for any security gaps that need immediate attention.
With Provision’s cybersecurity solutions, you can seamlessly monitor and manage across ten categories of risk: DNS health, patching cadence, web application security, information leaks, and social engineering. Contact us today.