The Internet of Things (IoT) is actively spreading around the world and is on the verge of a surge in development. Several factors contribute to this: 5G networks, Industry 4.0 or the Fourth Industrial Revolution, the growing possibilities of microprocessor computing – more on each of these below. The smart home systems, business and industrial segment of IoT devices have similar implementation problems – the lack of common standards, including documentation standards, lack of high-quality descriptions of protocols and connections and the corresponding high cost of analyzing the level of actual security, the lack of standards for protection functions and often enough lack of microchip resources for the good implementation of security functions (encryption, authentication, etc.). This article explais how to lower IoT risk in the future of 5G.
Factors of growth for the Internet of Things Segment
Gartner at the beginning of 2020 already noted the increasing interest of companies in experiments with a combined Internet of things in order to optimize their own costs. As the adoption of the Internet of Things expands, requirements to ensure the safe operation of devices and increased maturity in IT come to the fore. Gartner predicts in the corporate segment by 2024 75% of completed projects totally in the field of the Internet of things and blockchain and the launch on the market of more than 100,000 models of digital twins. Thus, by 2023, 70% of providers will have to reconsider their approach to IoT segment security. By the way, “Digital Twin” is a term whose first publication is attributed to David Gelernter in the book Mirror Worlds (1991), and the definition in scientific and industry publications is to Michael Greaves (2002). This is a virtual digital copy of a real asset that can be used for example to simulate and predict what happens to a physical asset under external exposure, or for partial replacement of the physical asset. This is often a hybrid model that combines digital and physical components. The modeling property for digital twins and, as a result, the ability to predict and reduce the risks of breakdowns and accidents for their physical copies have already brought this technology into strategic IT trends, especially among large and industrial enterprises. On the threshold of the Fourth Industrial Revolution (Industry 4.0), the involvement of digital technology in all production processes is inevitable. Which, in turn, is associated with certain risks, because in most drones, robots and other IoT devices for performing a point function, usually their own mechanisms for ensuring information security are uncultivated. Risks are multiplies by the frequent need for remote management of digitized industrial and other IoT facilities.
What impact will 5G networks have on the Internet of things? The main features of this generation of mobile communications are:
• uniformity of network coverage and mass machine communication,
• highly reliable connection with a very low data transfer delay, and, which is more important, the ability to connect a large number of devices to the network in one geo-location to the one cell,
• low power consumption and high energy efficiency,
• direct connection of IoT devices to the global network via the mobile Internet.
These factors make it possible to connect to the mobile network with a good communication channel almost anything that comes to mind: from sneakers and a kettle to any environmental sensor. And all devices can be controlled remotely, be able to get telemetry from them and produce the necessary analytics. This is a strong driver for the spread of IoT technologies in the areas of business and in everyday life.
With the convenience that comes, there are risks of leakage of personal and confidential information, such as:
• telemetry data (how often the owner of the shoe goes out for a walk, what is his favorite store, how many steps a day he walks, etc.),
• multimedia data (image from built-in cameras),
• internal environmental parameters (data from smart home devices), etc.
Also, the main risk for IoT devices in the world of 5G networks is a direct connection of devices to the Internet via a mobile network, and not a Wi-Fi network, as is mainly happening in current realities.
In turn, the IoT-systems themselves in terms of computing capacity are becoming more comparable with full-fledged IT equipment. Simply, if 15 years ago the TV was equipped with an Arduino like chip, which was able to memorize frequencies and switch channels, now it is a full-fledged processor of the level of the best smartphone five years ago.
In addition, the manufacturer understands that the user will always prefer convenience and ease of use than the presence of complex security features. For example, choosing the same TV, the main and often the only criteria will be the image quality and the availability of various functions of media content. As practice shows, even security incidents do not have a long-term effect on consumer demand, nor on stocks and the manufacturer’s reputation. In this regard, investing in expensive work to develop information security devices is not profitable for the manufacturer. And therefore, even now, such equipment often becomes botnet agents. Here is a case in point – in May 2020, Microsoft researchers discovered a large DDoS attack using LED consoles. Researchers found a rapidly growing (100 times per month) botnet that generates a DDoS attacks of up to 1 TB per week. Botnet agents were placed on LED panels – one of the simplest IoT devices. Moreover, vore than others was infected the corporate sector of devices, in particular, the largest Taiwanese business center.
The average cost of an Arduino chip in mass production is literally a couple of dollars, so its implementation in everyday life, even taking into account the integration work, will not significantly increase the cost of goods. In this regard, the appearance of such ordinary IoT-things on the market is only a matter of readiness of consumer demand.
More powerful devices (multimedia, etc.) use more powerful processors, for example, Raspberry Pi or even ARM. But to carry out the planned tasks, as a rule, less power is needed, which generates a resource surplus. At the same time, the introduction of security functions for the reasons described above is not economically feasible for manufacturers, but favorable for attackers: “extra” computing power can be used for their own purposes. The mass and physical prevalence of devices is an additional factor in the interest of hackers in IoT systems. Even proprietary languages used in the Industrial IoT segment (Industrial IoT – IIoT) can be used to enter malicious code, steal confidential information, etc. Given the trend towards remote monitoring and management of industrial systems, their interaction with the Intranet and the Internet is growing, and accordingly risks of interception of control over them by intruders or interference in the production process, up to creating an emergency accident.
Security issues of the Internet of things and approaches to their solution
The main problems of information security and the risks for IoT devices in a broad sense can be described in a few points:
• Lack of regular update mechanisms (especially for simpler devices).
• Lack of security features and secure protocols in the firmware of devices, lack of global standards in this area.
• Lack of security controls for the supplier and the supply chain (especially relevant for digital twins in the industry).
• Inattentive attitude of users to settings – most users do not change default passwords, do not turn on available security settings, etc.
• Direct connection of weakly protected devices to an open network (especially relevant with the introduction of 5G networks).
For the safe operation of the device, the following must be guaranteed:
• manageability, observability,
• regularity of updating as the main mechanism for fixing vulnerabilities,
• no data leakage.
Some mechanisms, for example, over-the-air updates (OTA), are already being implemented by manufacturers for sufficiently smart devices. For example, TV will remind the user of the need to update the firmware or software of the multimedia device. It is up to the user to accept the offer on time. Often, the service pack has already been downloaded, and the process will not take more than 1-2 minutes. Rollback mechanisms for unsuccessful updates are also implemented.
For commercial IoT infrastructures, there is a class of information security solutions. The review and the quadrant of solutions, based on the experience of use and user feedback for 2019 and 2020, were presented by several companies, in particular: Technology Group – Fig. 1 and 2, MachNation – Fig. 3 and 4. Each manufacturer of solutions for commercial IoT infrastructures offers a concept for use in industrial enterprises and commercial infrastructures, as well as for a Smart home. The main functions performed by the solutions:
• Orchestration, search and monitoring of IoT devices invisible networks.
• Analytics of “dirty” data of IoT devices, analytics of big data to find valuable information in them.
• Information security mechanisms: encryption and control of access to device data, continuous monitoring, management and audit of configurations.
• Some manufacturers (for example, AWS) in the service package offer an OS for microcontrollers (FreeRTOS) with built-in security features, as well as tools for creating IoT applications.
Fig. 1 – Comparison from Technology Group on overall User Experience
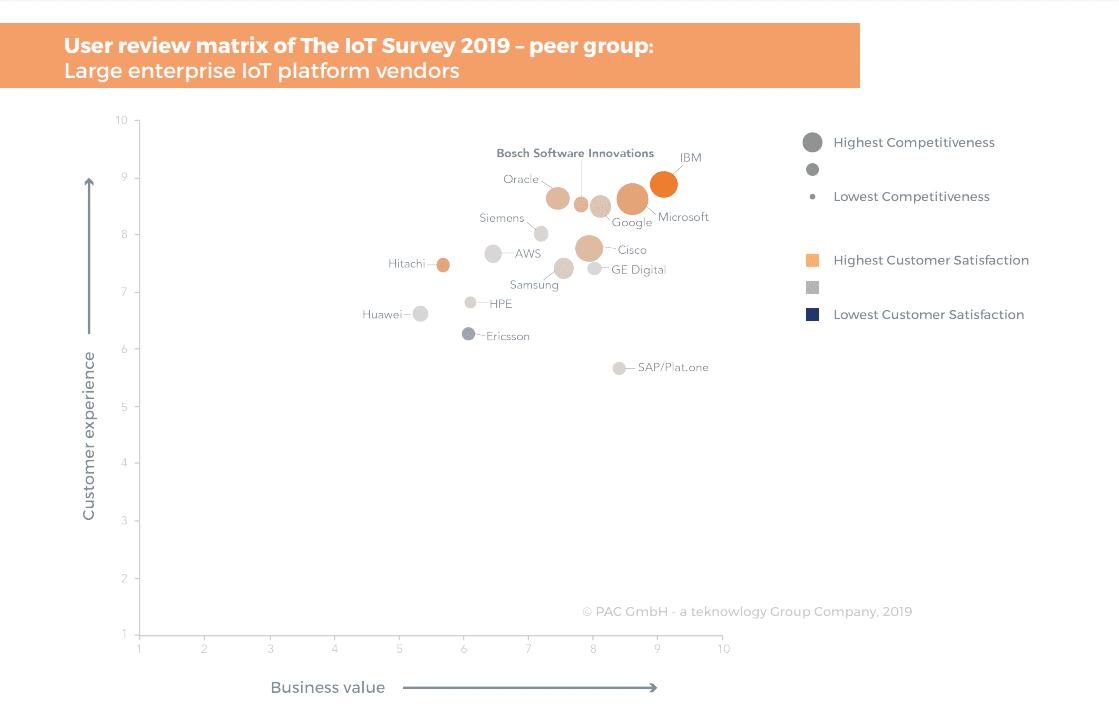
Fig. 2 – Comparison from Technology Group on the convenience of managing devices
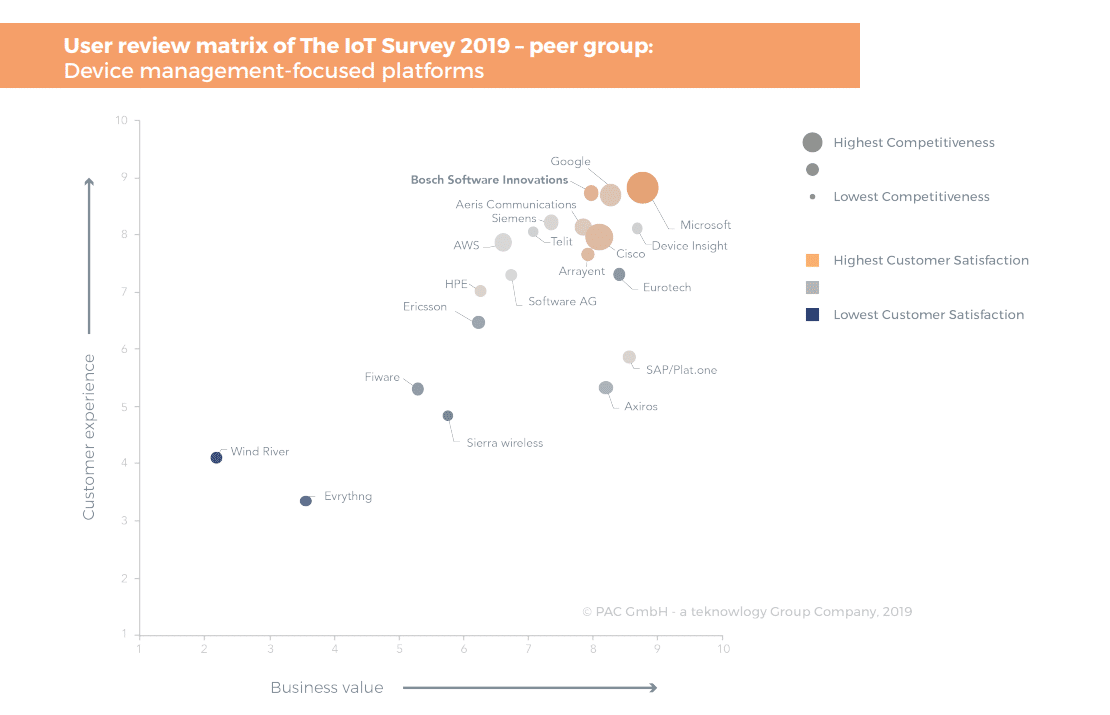
Fig. 3 – Comparison from MachNation for ease of management solutions
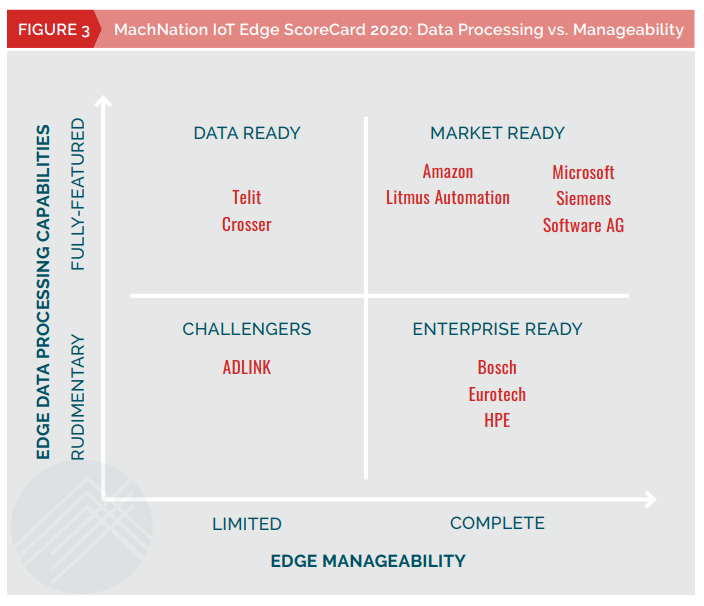
Fig. 4 – Comparison from MachNation on technology and business strategy
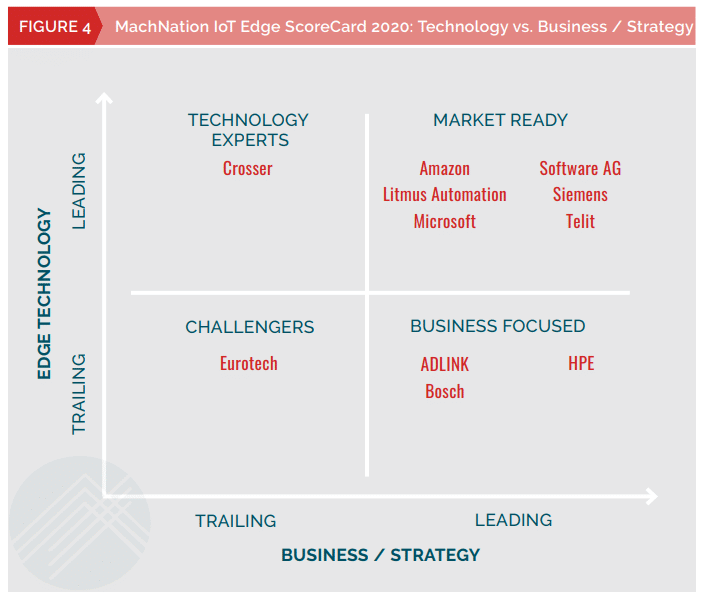
Gartner predicts that companies will increasingly acquire IoT-related security features, such as the expansion of general-purpose security products or the IoT platform. The choice of companies is more often directed towards universal IoT-security platforms than separate solutions.
Conclusions and recommendations to end users
Large manufacturing companies, small and medium-sized businesses are actively interested in IoT solutions and information security solutions for IoT infrastructure. This is an indicator of the active development of the market and the preparation of enterprises for a qualitative breakthrough in the digital sphere of the IoT market with the already prepared information security ground.
While commercial IoT deployments have the resources to find and implement mature approaches to information security, such resources are often inaccessible to the home user. What procedures can you use to protect yourself on your own when using new generation IoT devices:
• Ensure regular updates of firmware and software on the device – in any form: automatically or manually.
• Change default settings, first of all, passwords, including internal authentication,
• If there is a choice – use Wi-Fi or Bluetooth instead of a mobile connection, do not connect the devices to a shared network, select a separate segment for them on the router, use firewall shielding.
• Have a backup copy of the settings or image (depending on what is available on the device) for quick recovery in case of loss of control or functionality of the device.
• If the device operates in 5G mode and has contactless payment mechanisms, for example, smartwatches with integration with AliPay, then you need to understand the risks involved and, for example, use a dedicated card or bank account with limited funds, a withdrawal limit, operational tracking of payment transactions and possibly insurance against illegal operations.


